SIM swapping exploits make ID verification urgent

Financial crime takes many forms, but one of the fastest-growing threats is SIM swapping, a tactic that allows criminals to hijack mobile numbers and steal identities. While suspicious transactions can flag laundering activity, every financial crime begins with verifying that a person is who they claim to be – and what once seemed like a simple identity check has become a complex, high-stakes challenge due to technological advancements.
Not only are sophisticated face-mimicking tools on the rise, but illegal uses of everyday devices are also creating new vulnerabilities. SIM cards—a necessity for mobile users to access networks—have become both a huge illicit market and a regulatory blind spot. Lax identity verification (IDV) during SIM registration can ripple far beyond telcos, shutting down networks, disrupting city authorities, and exposing banks and fintechs to significant downstream risks.
More must be done to raise awareness and implement practical solutions, stressing the severity of SIM fraud and demonstrating how cooperative approaches to strengthen IDV could prevent irreparable damage.
The scourge of SIM Swapping
SIM cards play a larger part in identity theft than many would believe. A SIM card could be identified as an ‘access key’ to mobile services, but that grants permissions to access a wealth of personal information. After stealing personal information, attackers can ‘SIM swap’ or hijack identities by convincing a telco to port their number onto an illegal SIM card and gain a victim’s texts, calls, or security codes to a different mobile. The UK’s Cifas saw almost 3000 cases of this last year, a rise by 1,055%.
In South Africa SIMs must be registered with a network, requiring personal details, identity numbers and proof of address under the Regulation of Interception of Communications and Provision of Communication Related Information Act (RICA) passed in 2002. This has done little to mitigate SIM crime. Many nationals have multiple cards where 80% are discarded for better deals, leaving them pre-registered and open to abuse. Anyone could request a RICA-authorised SIM from a repair store.
It’s so tricky to trace communications to the criminals that RICA’s legally-obliging police interceptions and investigations become obsolete, enabling a loophole that can continue reaping illicit rewards for hackers.
SIM fraud on the larger scale
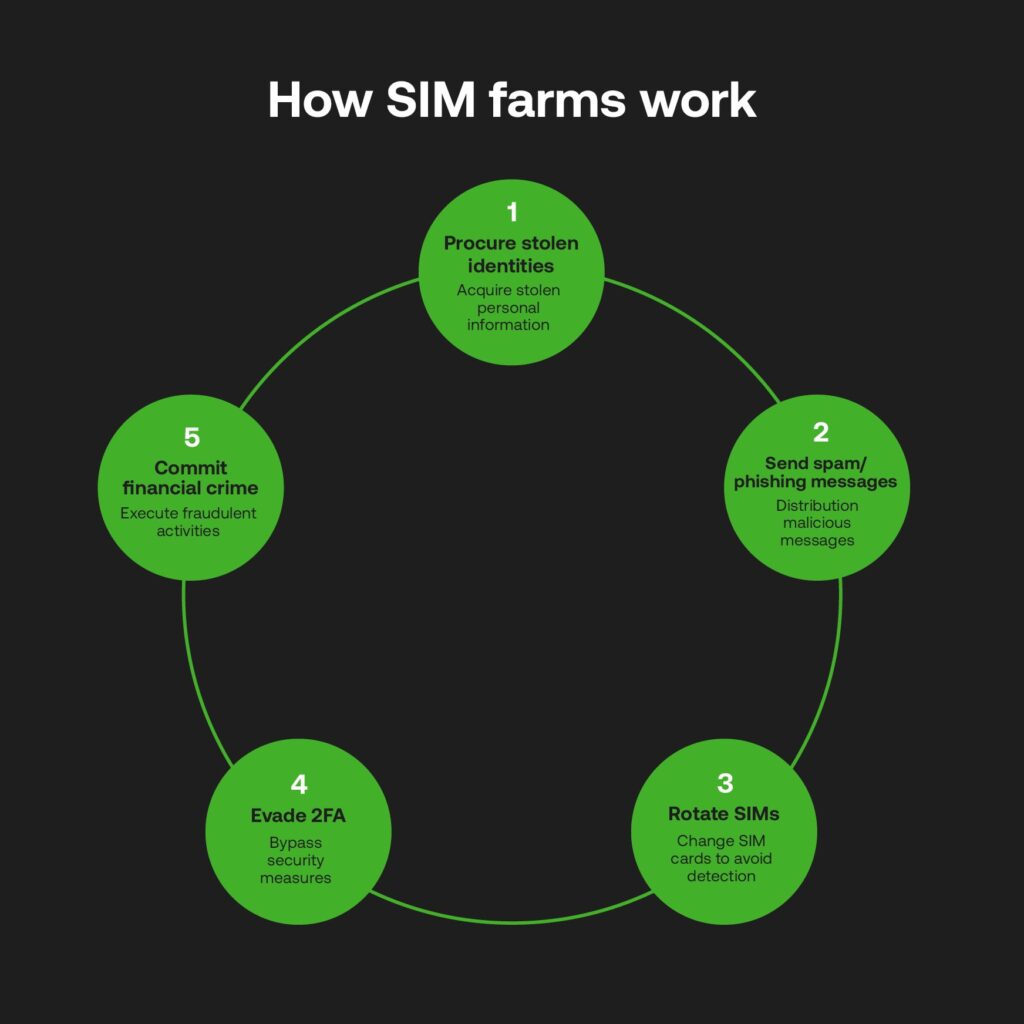
In some cases, clampdowns of illegal SIM manufacturing and distribution are successful, if only scouring the surface of the problem. SIM farms take criminality to new levels; even a single setup can launch widespread identity impersonation campaigns behind prepaid or stolen SIMs.
Favourable in co-located and effectively powered data centres, thousands of cards can be wired into servers to enable a vastly scalable operation to make overwhelming levels of contact with mobile networks. In New York, one SIM farm was able to overload traffic so much that emergency services struggled to cross-reference. While the UK looks to ban the supplies of SIM farm technical devices, it will become the first European country to do so.
Elsewhere, a WIRED investigation with a telecoms industry source identified how SIM farm technology is not just fast and voluminous, but crafty in masking criminality geographically through legitimate users, and – most scarily for telcos and financial businesses on the frontline of identity theft – by bypassing even advanced detection systems.
Where businesses underestimate IDV
These SIM farms are ultra-intelligent organised crime units with cross-border networks and online connectivity. They target mobile banking and investment apps, as found by Operation Red Card, led by Interpol, across seven African countries. Europol has also disrupted a criminal network accounting for almost €6 million in losses in Austria and Latvia. The fact that this entity operated as a ‘cybercrime-as-a-service’ speaks scarily to the agile business-like setups of these webs for nefarious gain.
The very companies that are required to safely conduct IDV are falling very far behind. Verification is a major onboarding step growing more difficult day by day considering the routes and chances granted by criminals and the very people they exploit – as with the given cases, there’s evidence that scam centre workers are coerced or trafficked, signifying how deep the stolen ID iceberg reaches.
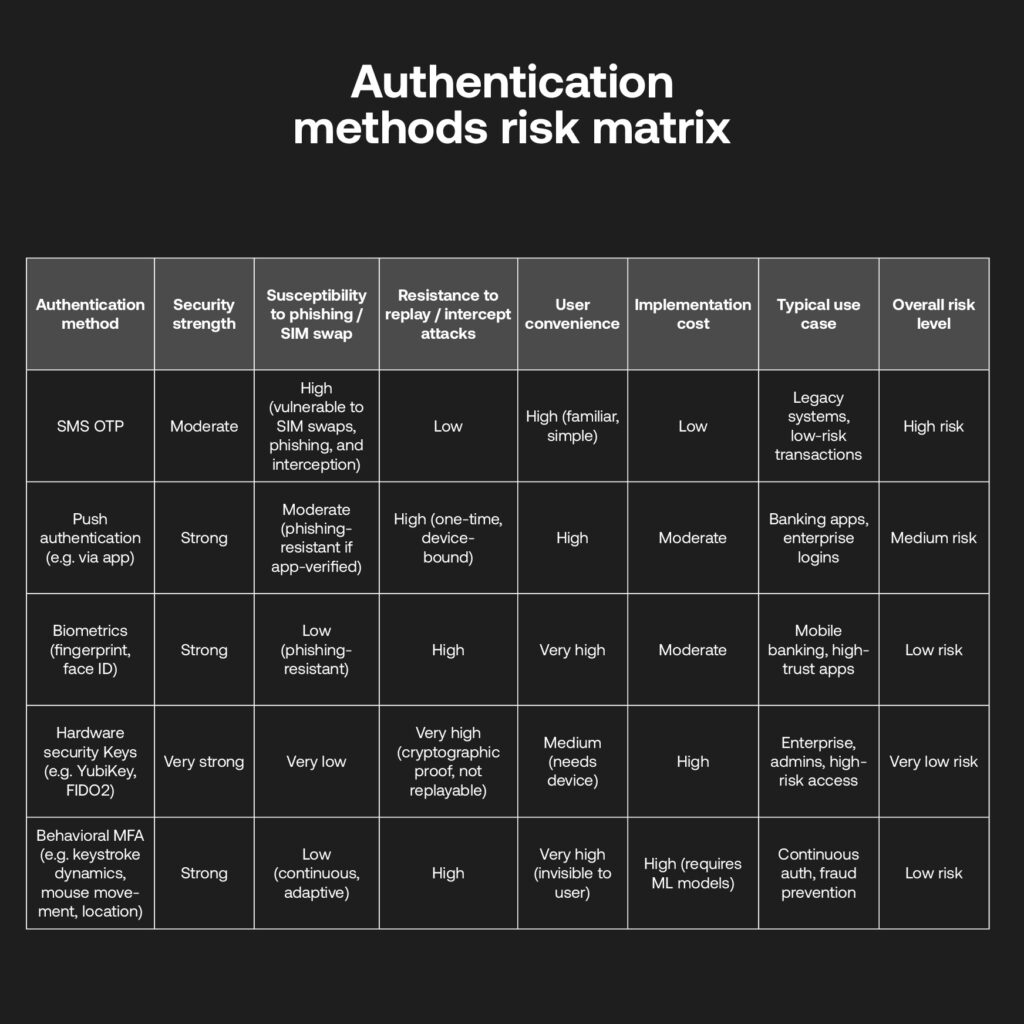
Every single illegal SIM in circulation accounts for a counterfeit identity, which puts into perspective how services that do not secure their IDV are essentially pouring gasoline onto a fire. For example, businesses are susceptible to slip ups using one-time passwords (OTP) for online verification; due to this method being linked to SMS as a two-factor authentication (2FA), SIM hackers can steal user data and personal finances through various apps.
This is also barely a cost-effective deterrent with banks spending tens of millions annually on pricey SMS OTPs, their ensuing false positives and failed deliveries, and know your customer (KYC) re-verification following SIM swapping activity. It’s far from enough to outsmart identity thieves business-wide, let alone on a global scale.
Are there better methods?
That’s not to suggest that multi-factor authentications (MFA) are ineffective. But they become more secure logins as a part of a company’s focused risk-based onboarding technologies:
- Although advanced deepfake techniques and injection attacks can curb biometric checks, such KYC tools limit cases of criminals trying to access phones without easily replicating a registered FaceID on many smartphones, tying a real video image to their account.
- AI-based IDV can detect even sophisticated lighting or textual nuances to catch manipulated images, too.
- Now that many businesses in financial services or otherwise are personalising digital experiences, they’re capturing marketing data in real-time, including identities, transactional histories and typical online behaviours. This also contributes to IDV, as such behavioural intelligence builds a picture of unique touchpoints tough for criminals to replicate.
- Push notification MFA can approve an action through a pre-registered device or app, without hinging on a vulnerable SMS network.
- Other apps such as Google Authenticator or tools such as hardware keys are not affiliated with phone numbers than the devices themselves, and less prone to SIM attacks.
These compliance considerations should be front-of-mind for any business improving their KYC, before the identity theft problem becomes a weight too heavy to handle.
A call for cooperation
It’s easy to view telcos, banks, insurers, and governments as separate entities all duly responsible to safeguard their users’ credentials. But siloed KYC operations are gaps these criminals look to for exploitation. All accountable institutions are united under a compliance ecosystem that must be proactive to catch threats before they proliferate, which depends on cross-sector collaborations and strengthened frameworks for KYC and anti-money laundering (AML) compliance, despite variations on data privacy legislation.
It should not be ignored how utilising regulatory technology to facilitate IDV is the starting point to catch anomalous behaviour, leading to investigations bringing mobile carriers, financial institutions, regulators and prosecutors together under shared intelligence. With users vetted instantly, customers can be onboarded fast while alerts can be dealt with through authorities that matter – all backed up by auditable reports.
Public perception around SIM crime is one aspect, boosting knowledge of their role in safeguarding their identities and contacting service providers for help. Better education and leadership stems from compliant businesses, and builds a greater network to combat SIM farm outlets that span regions throughout the digital underbelly, out of reach.
One weak link makes fraudsters stronger in a world where harnessing data can be a powerful superpower for wrongdoing – the ‘good’ side must band together through knowledge and technical RegTech capability to reclaim ID protection and halt this train before it steams ahead.


