Fraud chains, and the wider organised crime picture of investment scams

Investment scams are growing exponentially, and becoming more highly evolved traps since the days of traditional Ponzi schemes. In the UK alone, the first half of 2025 saw over £600 million stolen through scams and payment fraud, despite a further £870 million being stopped by banks.
While financial institutions’ defences are admirable, the sheer weight and sophistication of scam money movement threatens to topple those unable to detect and halt these flows. That’s also problematic given investment scams are not isolated events – they’re often the initial doorways into global organised crime financing, where one scam proliferates further crime downstream to affect more vulnerable victims. Instead, integrated intelligence marks the future of fraud prevention, as we explore here.
Understanding the fraud chain ecosystem
Criminality knows no bounds, exemplified by the fact that organised crime typically works as a fraud chain. Within these networks, specialised units can operate in hyper-focused markets, fully honing their craft and obscuring the entire franchise’s activities. Outsourcing great numbers of individuals ensures that financial crime typologies can be committed to scale, and the proceeds more easily hidden, repurposed and laundered through complex structures that fraud agencies and law enforcement are tasked with cracking.
The chain remains interconnected through bank accounts, digital wallets and online and offline channels, where this advancing digitalisation of financial instruments masks activity even more effectively. Typical actors within this ecosystem include social engineering scammers, launderers, corrupt banking or political insiders, money mules and crypto off-rampers – those who convert fiat currency into potentially unregulated digital assets.
Types of investment scams
Ponzi and pyramid schemes are already ‘household name’ investment scams, managing to lure early stage investors with promises of high-value commission until the funds dry up. However, a whole new swathe of avenues for deception are building to trick budding investors, as well as allude financial crime stoppers:
- Pig butchering: similar to long-term romance fraud, and taken from the Chinese “Sha Zhu Pan” (“killing pig game”), this involves scammers developing trust with victims before manipulating them into an investment scam often based on cryptocurrencies.
- Crypto investment schemes: Criminals can dupe victims with high returns made through fraudulent (but legitimate-looking) websites and social media accounts. They take advantage of crypto’s regulatory grey areas, and a lack of awareness from the general public, to demand fake taxes and fees.
- Fake trading platforms: Online trading platforms can scam investors with celebrity endorsements and lives of luxury, where a firm promises to make trades on their behalf, before encouraging larger investment sums and referrals until the returns stop.
- Insider tip scams: A type of betting fraud where criminals claim to be ‘in the know’ of specialist non-public information which will incur high returns and low (or no) risk levels, which all proper investments should carry.
Scammers are even setting up investment fraud companies through legitimate offices, marketing literature and platforms, yet establishing crypto wallets and bank accounts using victims’ own details on the sly to keep a laundering network functioning, even after the investment scams stop. It means exploited individuals unwittingly start facilitating further crime against others.
Investment scams are attractive not just for being lucrative – with long-term relationship building and manipulation often resulting in big-money transfers – but roped-in victims roped into wider schemes make for a brilliant cover for nefarious means. Through repeated targeting, the same people can ship funds across borders or through digital payment rails that are increasingly difficult for banks and payment services to block.

A typical fraud-to-laundering pipeline
There’s a misconception that it’s only the victimised investors in these acts that are affected. Investment scams are often a stepping stone into far murkier criminal territories that impact people all around the world, done so through staggered and layered laundering techniques.
- Victim transfers
For pig-butchering or romance scams that attempt to gain vast sums of money from vulnerable people, victims are found through dating websites and social media, eventually enticed to pay the scammer through payment platforms or digital wallets that seem like credible channels.
- Money mule accounts
A key indicator of modern laundering is when criminals harvest even more from these initially manipulated victims through muling. Mules are often recruited through job advertisements, student networks and social media promising large earnings, mostly to young people. In fact, almost half of 18 to 24 year olds in the UK have been targeted by such a scam, or known someone who has. 60% are contacted via SMS or messaging apps.
Launderers get mules to do their dirty work, divvying up assets to make digital trails fragmented, and can operate interdependently in all areas of the world. They may access multi-location accounts using VPNs or hesitate to update their KYC data. As mules tend to have no criminal record, financial institutions deem them low-risk customers, and their transactions often go unnoticed.
- Layering techniques
Operating through multiple banks and accounts, and through under- or over-valued amounts or microtransactions, laundered funds can move rapidly throughout the system undetected. Spotting dirty money is becoming even more difficult with crypto off-rampers converting payment types into newer forms, such as stablecoins, and where crypto tumblers can pool funds from various accounts that obscure the origins and destinations in a multi-path money trail.
- Integration for organised crime financing
These investment scam proceeds fuel vast syndicates that control terrorist financing, arms rackets, human trafficking, and drug distribution. The monies can buy weapons, run illegal factories, and purchase illegal passports and fraudulent documents – showcasing the harsh real-world impact even one-time scams create.
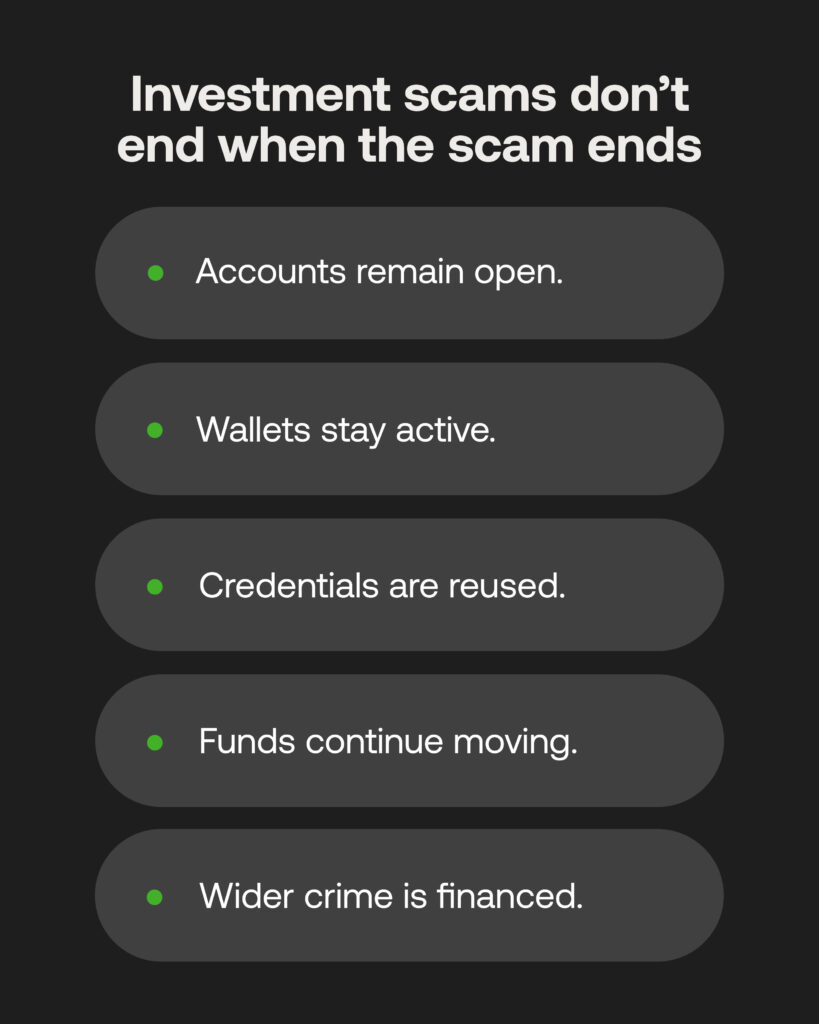
Siloed scam detection: The problem for anti-fraud teams
Of course, with investment scams being a money business, financial institutions they bank with are tasked with spotting the criminals at the source. This is easier said than done given the aforementioned obfuscation techniques, as well as the sheer number of digital transactions that happen – spotting high-value transfers, or unusual or uncharacteristic behaviours from manipulated customers is near-impossible among the noise, and without advanced AML software linking people to payments.
While fraud and AML teams have been treated as separate functions, their dual mission of spotting red flags is finally seeing a greater convergence – albeit not across the board. Anti-financial crime systems they use have to maintain oversight over customer onboarding, screening, incoming deposits, rapid transfers, crypto on- or off-ramping behaviours, and linked accounts under different names.
Fraud chains are cross-functional and overlap the tasks for AML and fraud teams, where that gap between the two defences allows them to remain undetected. Often fraud teams will focus on the victims’ cases, while AMLs instead look into suspicious mule activity, for instance. Detection across the entire digital fraud lifecycle has to be centralised for all potential stages of the deception to be stopped in its tracks; not just within an AML system, but with protocols shared by collaborative teams.
Sharing data to break fraud chains
With a single source of truth used to enact risk-based AML approaches, craftily shrouded funds between investment scammers, victims, mules, and potentially beneficiaries or organised crime can be spotted in real-time, and links made between criminals and the areas, people, and organisations they choose to manipulate:
- Unified risk signals: by setting high-risk scores for customer types and transaction types, fraud and AML teams gain immediate insight into potentially fraudulent activity. Shared risk scores through common attributes (contacts, IP addresses) also reveal links when direct relationships aren’t explicit. A flagged mule account for AML investigations may tie back to a known scam in this way.
- KYC and behaviour monitoring: picking up suspicious mule-alerts at onboarding relies on implementing high-risk factors into workflows, while continually picking up changes in any customers’ risk profiles – such as accounts only being used to shift funds, often internationally, or irregular or large deposits – can discover bad actors out of huge datasets.
- Network-level risk insights: consolidating risk profiles, transactions, devices and IDs using entity resolution helps report individuals, and even whole organisational structures, that may be involved in scams. This speeds up the investigation-to-prosecution pipeline, and unites accountable institutions through tracked data.
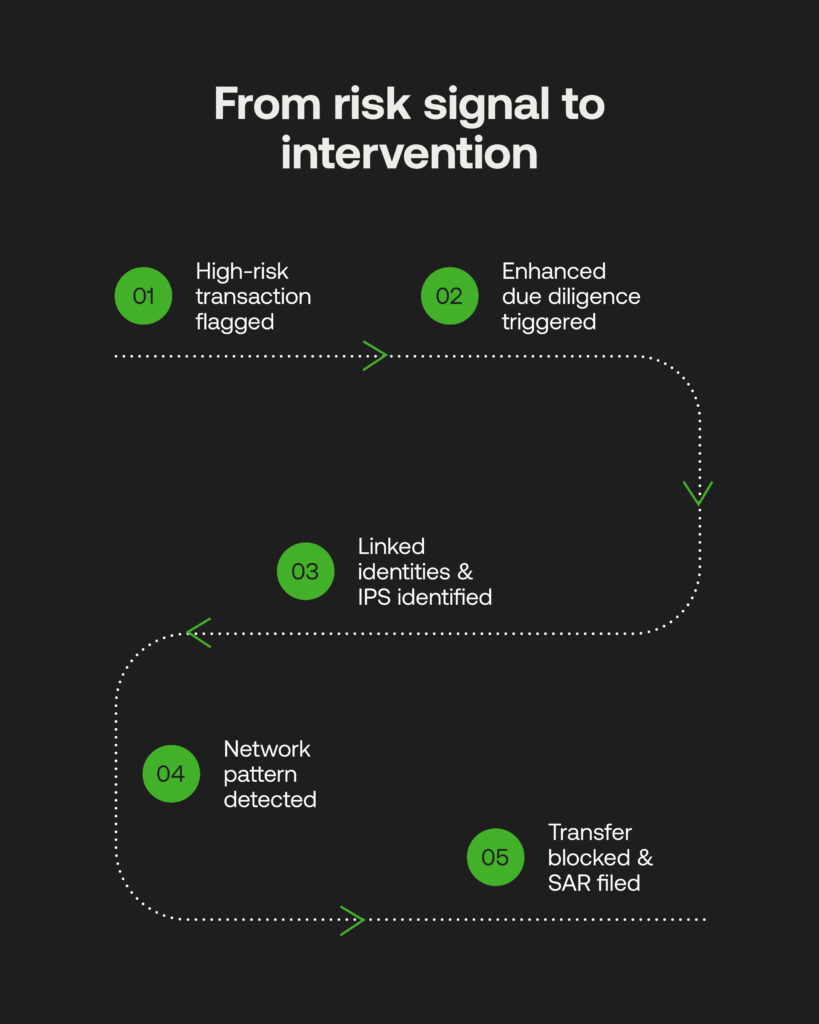
As a high-level example, an integrated AML platform could flag an incoming transaction as high-risk. During enhanced due diligence, a compliance analyst would then check for further intelligence of linked identities or red-listed IP addresses. When the same risk alert has a suspicious pattern for low incomings and outgoings to various institutions, network analytics can be leveraged to uncover the broader strands of individuals, beneficiaries and shell companies involved. The transfer can be blocked, while automated SAR reporting helps aid law enforcement to catch investment scammers.
Stop investment scams, stop wider crime
As if investment scams were not already low and exploitative, zooming out further identifies how they start a domino effect of highly curated criminality. The various steps scammers take are all planned, and will continue to infiltrate AML and fraud gaps financial institutions have if they remain blind to evolving methods, or fail to improve intelligence storing and sharing.
Collaboration through compliance teams, fraud specialists, regulatory leaders and law enforcement is absolutely paramount, connected through audited data that has the power to stop investment scams fast. Understanding fraud chains and the criminal mentality is the beginning to make up for AML shortcomings, yet it’s the appetite to better implement technology that will make taking action against vast, dangerous gangs both targeted and effective. The safety of the financial world depends on it, before the criminals move onto their next phases before too long.
To learn more about investment scams, listen to our latest podcast episode of Laundered featuring Gareth Dothie, a former City of London Police detective.


