Achieving AML compliance

Table of Contents
- What is AML Compliance?
- The importance of AML compliance in 2025
- Reputational and business impact of non-compliance
- Understanding the 3 stages of money laundering
- Industry-specific AML compliance requirements
- 10 essential steps to achieve AML compliance
- Step 1: Appoint a qualified AML compliance officer
- Step 2: Conduct comprehensive Risk Assessment
- Step 3: Develop robust AML policies and procedures
- Step 4: Implement effective Customer Due Diligence (CDD)
- Step 5: Establish advanced Transaction Monitoring
- Step 6: Master Suspicious Activity Reporting (SAR)
- Step 7: Deliver comprehensive staff training
- Step 8: Maintain detailed records and documentation
- Step 9: Conduct regular independent audits
- Step 10: Stay current with regulatory changes
- Common AML compliance challenges and solutions
- Building a robust AML compliance programme
Anti-money laundering (AML) regulations are getting more complex, but companies and financial institutions must comply to avoid steep penalties and reputational damage. This comprehensive guide provides details on achieving AML compliance.
What is AML Compliance?
AML compliance refers to the policies, procedures, and controls governments implement to detect, prevent, and report money laundering and terrorist financing. It encompasses all the tools and systems used to adhere to anti-money laundering laws and regulations, with rules tailored to individual needs.
Core Components of AML Compliance
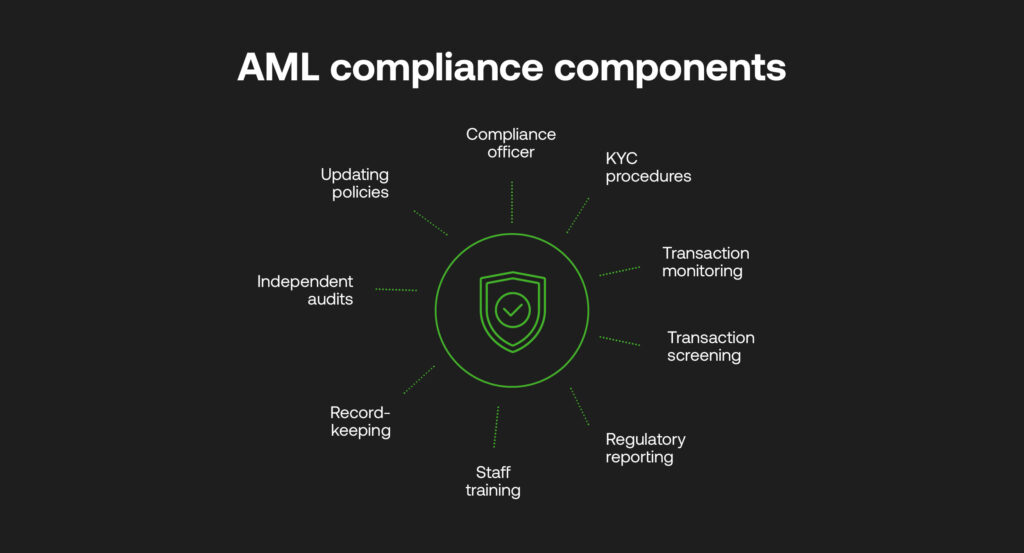
Some critical elements of an AML compliance programme include:
- Appointing a Compliance Officer: Having a qualified professional responsible for managing AML compliance is the foundation of any strong programme.
- Know Your Customer (KYC) Procedures: Collecting client information to verify identity, nature of business, source of funds, and to assess risks.
- Transaction Monitoring: Ongoing monitoring of customer activity and transactions to identify suspicious behaviour.
- Transaction Screening: Assessing various payment types, formats, contexts and countries against trusted worldwide databases.
- Regulatory Reporting (SAR, STR, CTR): Filing reports on transactions or attempted transactions and those that display red flags to relevant authorities.
- Staff Training: Educating employees across the company about AML and their obligations.
- Record-Keeping: Maintaining documentation related to compliance processes and analyses.
- Independent Audits: Conducting unbiased periodic reviews of the AML programme to assess effectiveness.
- Updating Policies: Reviewing procedures regularly and adjusting to emerging risks and regulatory change.
Legal framework and regulatory bodies
Global standards for achieving AML compliance are overseen by the Financial Action Task Force (FATF). It upholds how each country facilitates its anti-fincrime measures through an intended international framework of Recommendations that aid the combatting of money laundering and terrorist financing.
Individual regions, jurisdictions and nations however have their own regulatory agencies to promote the integrity of their financial ecosystems through their approaches to AML and CTF, following rules and regulations of their governments and FATF’s measures.
The strictest AML regimes are typically found in the US (Bank Secrecy Act, USA PATRIOT Act), EU (6th Anti-Money Laundering Directive), UK (Proceeds of Crime Act), and Singapore (Anti-Money Laundering Act). These jurisdictions have comprehensive requirements, significant penalties, and active enforcement. Emerging markets often have developing frameworks with varying enforcement levels.
AML vs KYC: understanding the difference
While AML is a multi-faceted approach that combines policy, programmes and technologies, KYC checks exist as one of the many necessary steps to identify, raise and report any suspicious entities or activities within a customer base.
KYC is typically an initial due diligence step within an AML workflow that verifies information for a legitimate customer to continue to transact with a financial institution, while perpetual KYC (pKYC) involves automations to continuously monitor customer risk profiles for any anomalous behaviours.
The importance of AML compliance in 2025
Ultimately, robust AML processes protect the integrity and stability of the financial system. Firms that fail to comply risk heavy fines, lawsuits, revocation of licences, and severe reputational damage, allowing financial crime to continue to threaten the world at large.
Global money laundering statistics and trends
The estimated scope of global money laundering is $1 to $2 trillion annually, between 2% and 5% of the world’s GDP, as estimated by the United Nations Office on Drugs and Crime (UNODC).
This can increase rapidly without AML compliance in place. Beyond traditional laundering techniques, technological advancement is seeing emerging threats through the use of cryptocurrencies, digital assets and wallets, decentralised ledgers, generative AI (GenAI), deepfakes and identity fraud.
2024/2025 high-profile AML penalties and fines
Anti-money laundering compliance is imperative for a range of businesses, from traditional banks to emerging startups. The scale of recent AML fines and their scope to include a range of accountable institutions shows this, including the following:
- Capitec Bank: In 2024, SARB administered sanctions against Capitec Bank amounting to R56 million for inadequate KYC, enhanced and ongoing due diligence, and failing to attend to transaction monitoring alerts.
- TD Bank: settled a $3 billion charge from the US Treasury and US Justice Department for faults in monitoring money laundering tied to drug cartels in 2024.
- Klarna Bank: last year the Swedish company was fined $46m by the Financial Supervisory Authority (FSA) for gaps in being able to identify potential AML/CTF practices.
- OKX: one of the world’s oldest crypto exchanges was fined £505m for breaking US AML laws, including flushing $5 billion worth of criminal proceeds.
Reputational and business impact of non-compliance
Non-compliance can result in severe penalties, including monetary fines (often millions to billions of dollars), criminal charges against executives, license revocation, business closure, and ongoing regulatory supervision.
Beyond financial penalties, companies face reputational damage, customer loss, and difficulty obtaining banking services.
Understanding the 3 stages of money laundering
As money laundering allows criminals to conceal and legitimise illegal proceeds, understanding how laundering works can help identify suspicious financial activities. Let’s examine the three main stages of money laundering in greater depth.
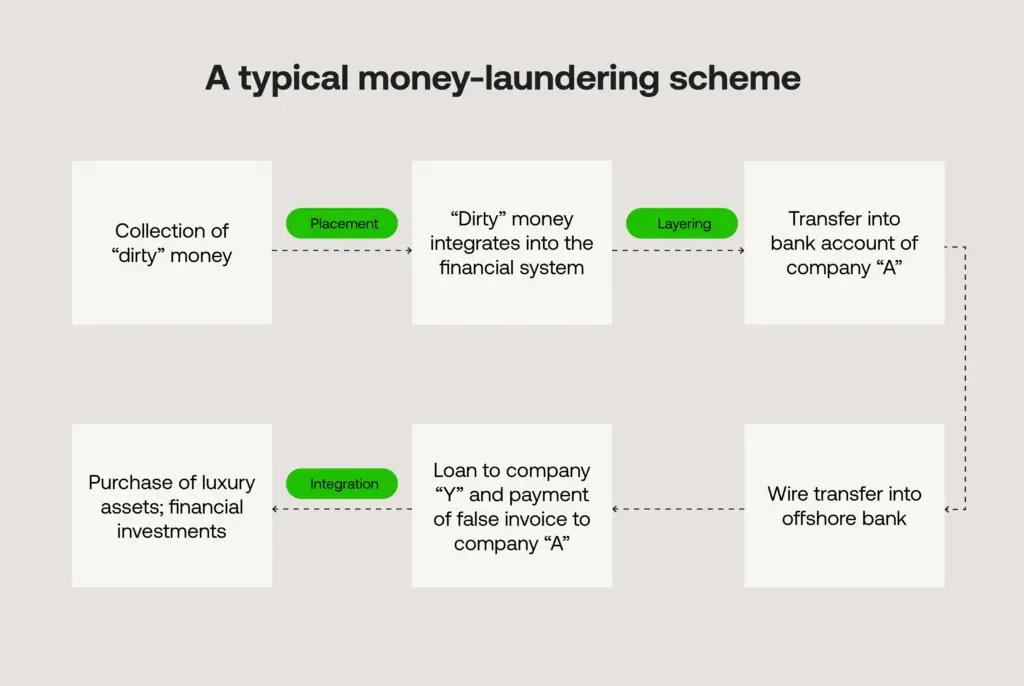
Stage 1: Placement – getting dirty money into the system
The first step in money laundering is placement, which involves introducing proceeds obtained through illegal activities – into the legitimate financial system.
Placement enables launderers to surreptitiously introduce “dirty cash” into banks and accounts, although significant, unexplained cash deposits often trigger anti-money laundering alerts.
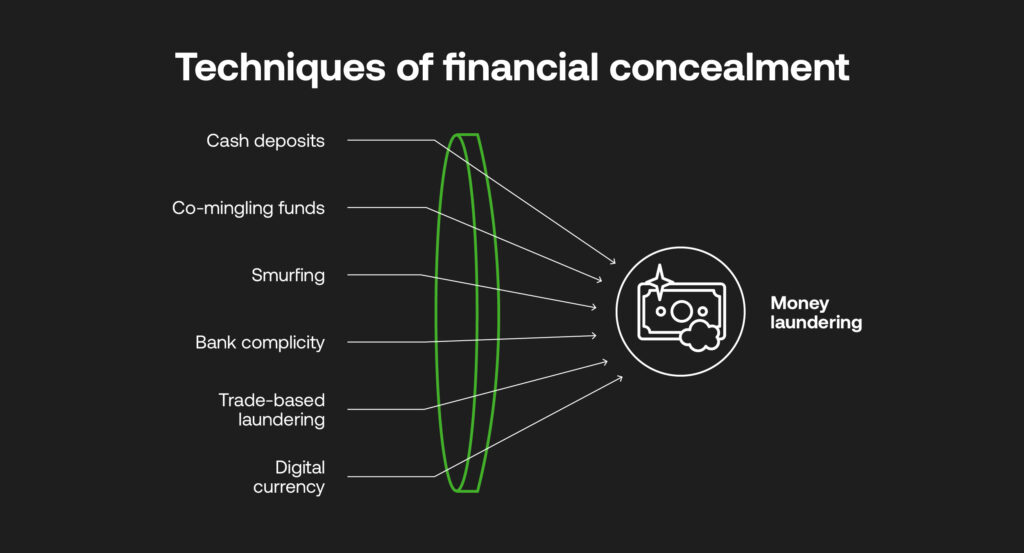
Common Placement Methods
These include:
- Making cash deposits: This remains a prime technique despite the risks. Launderers make multiple smaller deposits below reporting thresholds at various bank branches. However, banks must report unusually large or frequent cash transactions.
- Co-mingling with legal funds: Launderers open legitimate businesses like restaurants, launderettes, or retail stores and mix illegal cash into revenues, justifying cash deposits.
- Smurfing: A cash amount is divided into smaller sums and distributed across many accounts, deposited by various “smurfs” to evade suspicion.
- Bank complicity: In some instances, corrupt bank insiders facilitate illicit cash deposits and ignore reporting duties, heightening risks to the financial system.
- Trade-based laundering: Misrepresenting trade transactions, like over- or under-invoicing imports or exports, allows transferring funds across borders
- Digital currency placement: anonymous or pseudonymous identities make it tough to identify origin of funds, while decentralised regulations allow payments to operate without the gaze of central authorities.
Stage 2: Layering – obscuring the money trail
The second step is layering, where the funds are moved through a complex web of transactions to obscure the audit trail back to the illegal source. The more layers created, the harder it becomes to link funds back to the original illicit activity.
Complex layering, therefore, is a hallmark of sophisticated money laundering schemes.
Layering techniques include:
- Making multiple transfers across accounts and institutions, domestically or globally, spreading funds geographically.
- Wire transfers between shell corporation accounts. Fictitious businesses mask transfers.
- Overpaying invoices and returning the excess amount creates the illusion of legitimate transactions.
- Changing the money’s currency through trades or exchanges further dissociates it from the source.
- Purchasing high-value assets like gold, art, and real estate changes the form of the funds.
- Gambling the money and requesting casino payouts creates justification for large, suspicious transactions.
- Funds can be made between different cryptocurrencies to obscure tracking efforts, made even more difficult with privacy coins.
- Services called ‘mixers and tumblers’ split up and refigure identifiable transactions.
- Electronic transfers across different bank accounts in various jurisdictions can hide beneficial owners.
Stage 3: Integration – legitimising criminal proceeds
The integration phase places the laundered proceeds back into circulation in the legitimate economy, allowing criminals to use the funds openly.
Typical integration techniques used are:
- Transferring layered funds back into personal or business accounts, often to jurisdictions and entities with weak AML monitoring.
- Cashing out investments bought with laundered money, For example, spending extravagantly on stocks, bonds, and property.
- Spending laundered funds on yachts, luxury items, vacations, and property.
- Loans, mortgages, or business investments using shell companies that received layered funds.
- Cryptocurrencies can be transferred into fiat currency using exchanges.
After successful integration, the criminal origins of the money become near-impossible to find, and the launderers can now spend or reinvest the funds in further illegal activity.
Industry-specific AML compliance requirements
Financial institutions are not the only businesses that face scrutiny from both FATF and jurisdictional authorities.
While different countries will vary which they consider high-risk industries according to their own risk levels and legal systems, more and more sectors are finding themselves accountable for achieving AML compliance to a high degree. FATF separates financial businesses and Designated Non-Financial Businesses and Professions (DNFBPs):
Financial Institutions include banks (commercial or investment), insurance companies, credit unions, lenders, fintechs, and subsidiaries.
DNFBPs include real estate, non-profit organisations (NPOs), accounting firms and auditors, legal professions, motor vehicle dealerships, casinos and gambling companies and high-end goods (jewellery, precious metals, art, antique, etc.).
FATF is also encouraging the supervision of virtual assets and cryptocurrencies.
10 essential steps to achieve AML compliance
Step 1: Appoint a qualified AML compliance officer
Key qualifications
A skilled and experienced professional as an AML Compliance Officer can lead your compliance programme, equipped with relevant qualifications, knowledge, and access to resources.
AML Compliance Officers typically need a relevant bachelor’s degree (finance, law, business), professional certifications (CAMS, ACAMS, ICA), 5+ years AML experience, regulatory knowledge, analytical skills, and leadership experience. Many jurisdictions require specific training hours and ongoing education. Large institutions often prefer advanced degrees and specialised expertise.
Responsibilities
Appointing a Chief Compliance Officer who reports to the board demonstrates that AML compliance is taken seriously, and regulators will assess if this person has sufficient authority, resources, and skills. The Compliance Officer’s responsibilities include:
- Developing AML policies, procedures and controls
- Overseeing client due diligence and onboarding
- Managing transaction monitoring systems
- Reviewing suspicious activity alerts
- Deciding which Suspicious Activity Reports (SARs) need to be filed
- Arranging necessary AML training for staff
- Keeping board and senior management informed on compliance updates
- Conducting risk assessments to identify and implement programme gaps
- Testing and updating the AML programme periodically
Step 2: Conduct comprehensive Risk Assessment
Risk Assessment methodologies
A detailed risk assessment involves identifying and prioritising potential money laundering and terrorist financing vulnerabilities based on their threat levels. This can be done according to specific assets, or high, medium and low levels of risk with quantitative or qualitative measures determined by a business.
Common risk factors
- Nature of customers and counterparties: Risk profiles based on type of business, location, reputation, nature of transactions, etc. Higher-risk clients like offshore companies, PEPs, casinos, or arms dealers require enhanced due diligence.
- Products and services: Anonymous or cash-intensive products, such as private banking or wire transfers, are particularly vulnerable. Always assess the risks of new products before launch.
- Channels and interfaces: Online, mobile, or telephonic channels pose higher risks than brick-and-mortar channels due to fewer physical interactions.
- Locations: Countries with lax AML laws or those involved in conflicts pose higher risks.
- Assess risks posed by new technologies, outsourcing practices, or acquisitions.
Ongoing Risk Monitoring
Risk assessments should be updated regularly to reflect changes in products, services, risks, and regulations.
Step 3: Develop robust AML policies and procedures
Policy framework best practices
Draft clear, written policies and procedures that align with your risk assessment and resources. It must cover all critical AML areas, and be easily accessible for teams to cross-reference––via a secure portal, for instance.
It is also essential to ensure AML policies are comprehensive and regularly updated to account for new risks, regulations, and the outcomes of audits or inspections. They need approval from the board and senior management.
Documentation requirements
- Client Due Diligence: Procedures for identifying clients, verifying identity, screening for PEPs and sanctions lists, establishing the purpose of the relationship and source of funds, etc. Enhanced checks are required for high-risk categories.
- Transaction Monitoring: The process for monitoring client activity to detect suspicious transactions should outline transaction types, threshold timeframes, and systems for monitoring.
- Reporting Suspicious Activity: Define the process for analysing alerts, determining which are reportable, and escalating potential SARs to the Compliance Officer for filing with the Regulator.
- Record Keeping: Policy for maintaining detailed records of client information, account activity, transactions, risk analysis notes, investigations, regulatory reports, etc., in compliance with data privacy laws.
- Staff Training: Role-wise training on AML obligations for employees across departments, including new staff onboarding
- Independent Audit: Guidelines for conducting internal and external audits by third-party experts to assess the functioning of the AML programme, including frequency of audits.
Step 4: Implement effective Customer Due Diligence (CDD)
Standard CDD procedures
CDD lays the foundation for spotting red flags. Poor KYC is often cited in penalties against banks and companies for AML lapses as regulators continue to assess the adequacy of CDD policies and procedures.
Rigorous CDD processes should be established during onboarding, with KYC review aligned with the risk level, as follows:
- Identify clients and verify their identity using reliable documents, data, and reference checks. Screen against PEPs, sanctions lists, and adverse media.
- Understand the nature of the client’s business, occupation, location, expected transactions, source of funds, and purpose of the relationship to develop a risk profile.
Enhanced Due Diligence (EDD) requirements
Ensure a risk-based approach; higher-risk clients should undergo EDD, and changes in the risk profile should be identified promptly.
Ongoing monitoring and updates
Conduct ongoing monitoring of client activity against expected behaviour and update KYC details periodically, with enhanced ongoing CDD for high-risk clients.
Step 5: Establish advanced Transaction Monitoring
Transaction Monitoring Systems
Ongoing transaction monitoring and risk-based alert resolution are vital in detecting behaviour indicative of money laundering. Leveraging artificial intelligence, data analytics, and AML software can help monitor transactions across customer accounts in real-time and periodic batches.
Alert management and investigation
- Define scenarios like volume spikes, threshold breaches, counts of cash transactions, wire transfers to high-risk countries, etc., that will generate alerts for review.
- Your custom alerts should involve risk elements such as the client, product, jurisdiction, and bank.
Threshold setting and calibration
- High-risk scenarios should have stricter thresholds.
- Devise protocols for reviewing alerts and escalating potential SARs to the Officer with analysis notes.
Step 6: Master Suspicious Activity Reporting (SAR)
It’s imperative to file timely, complete, and accurate SARs on transactions over set thresholds and those displaying red flags that cannot be reasonably explained.
While SAR reporting differs around the world, the goAML is a fully integrated software for compiling audit-ready SARs, built by the UNODC and recognised as standard by multiple nations.
SAR filing requirements by jurisdiction
Authorities require deadlines for SAR submissions in relevant geographies, including the NCA in the UK, or the FIC in South Africa which should be checked regularly.
Quality control and review processes
- Include all key transaction parties, like the account holder, beneficiaries, counterparties, and locations.
- Maintain thorough records of all SARs filed, analyses performed, management notes, etc., to demonstrate rigour during audits.
- Review past SARs periodically for any follow-up required internally and, if necessary, with law enforcement
Step 7: Deliver comprehensive staff training
Role-based training programs
- Conduct well-planned AML training programmes across departments covering AML laws, internal policies, and the latest regulations.
- Risks, flags and new typologies should be tailored by job role, for example, customer-facing, operations, product, technology, etc.
- It is helpful to guide staff on what constitutes suspicious activity and when to escalate it to management and/or the Compliance Officer for reporting.
- Have a senior executive or manager reinforce a compliance culture.
Training effectiveness measurement
- Include assessments to check and ensure staff understanding. Track attendance and results, as failure to report can result in penalties.
- Repeat timeously to ensure staff are updated regularly with real examples relevant to the organisation.
Step 8: Maintain detailed records and documentation
Record retention requirements
Be sure to hold all client information securely, including transaction analysis reports, investigation notes, regulatory filings, and other documents that will be relevant to authorities. The more thorough the documentation of compliance processes, the more effective AML compliance success can be demonstrated to regulators.
Organise records for easy retrieval – client files, SARs, etc – and digitise records to store them securely, i.e. in an internal portal or cloud-based software.
Data security and privacy considerations
Implement access controls and data security measures in line with internal information security policies.
Store records for a stipulated duration based on jurisdictional laws (5–10 years typically) and destroy records irretrievably after the retention period ends.
Step 9: Conduct regular independent audits
Both internal and external audits by qualified third-party consultants should be performed regularly to assess the adequacy of your AML programme and include the following areas to audit:
- Process walk-throughs – KYC, transaction monitoring, reporting, etc.
- Policy and procedure documentation
- Risk assessment methodology
- Resources, including staff skills and tools/systems used
- Reporting and record-keeping
- Testing of scenarios with sample client data
- Evaluation of training programmes
- Sample file reviews
- Governance and management oversight
Once gaps, deficiencies, and areas for improvement are identified during each audit, it’s easier to define corrective measures and follow up on their implementation.
Step 10: Stay current with regulatory changes
As AML regulations evolve, staying up-to-date relies on monitoring regulatory notices, enforcement patterns, and industry events.
Regulatory monitoring strategies
- Seek legal/consulting advice to clarify new obligations.
- Increase vigilance for new high-risk threats.
- Evaluate the impact of new laws or changes in existing rules on policies and procedures.
Implementation of updates
- Enhance monitoring scenarios and systems to align with emerging typologies.
- Test preparedness and implement preventive controls proactively before regulations take effect.
Common AML compliance challenges and solutions
False Positive Reduction in Transaction Monitoring
False positives relate to low-risk alerts that are wrongly labelled as suspicious. Traditional systems can generate false positive rates up to 95%. AI-led transaction monitoring lowers this possibility by identifying high-risk according to user-set risk thresholds, reducing the time spent investigating legitimate payments.
Cross-Border Compliance Complexity
Differences in regional regulations, data privacy laws, currencies and other payment types can create roadblocks for identifying dirty cash in the global financial system. Risk-based approaches utilising advanced translation monitoring systems can identify potential criminality through various payment formats and account for jurisdictional AML frameworks.
Resource Constraints and Cost Management
Siloed systems create costly repeated workflows and investigations into false positives, while faulty AML can lead to extensive fines. For compliance teams of any size, integrated RegTech provides a comprehensive solution that lowers the total cost of ownership, uniting case management, data sharing and each integral stage of compliance that boosts efficiency and reduces the chances of failing regulatory expectations.
Data Quality and Integration Issues
Managing data in one platform ensures its security, while advanced AML platforms can be integrated with trusted third parties to ensure collected data is up to date. pKYC continuously updates customer risk profiles so that no potential harmful activity is missed.
Keeping Pace with Regulatory Changes
AML platforms have to be proactive when financial crime and regulations continue to evolve. Cloud-based systems offer the agility to scale AML operations from KYC through to SAR reporting, where risk models can be customised to stay in line with new threats and expectations. Risk-based approaches and RegTech partnerships allow businesses to continuously improve their AML strategies when needed.
Building a robust AML compliance programme

Money laundering constantly tries to stay one step ahead. With these steps, it’s possible to identify global trends and requirements to then adapt an AML compliance programme fit for any sized businesses. Adhering to the mandatory compliance is only the start. Innovative technology can take achieving AML compliance to the next level, with automations, smarter decision making and cooperative partnerships upping the standards for global AML – appeasing regulators and clamping down on notorious emerging criminal threats.
RelyComply’s AI-driven AML software solution offers robust transaction monitoring, customer risk scoring, KYC/KYB workflows, sanctions screening, and more. To discover more about our platform, arrange a demo with our team today!
Disclaimer
This article is intended for educational purposes and reflects information correct at the time of publishing, which is subject to change and can not guarantee accurate, timely or reliable information for use in future cases.