How Criminals Exploit KYC Vulnerabilities and Loopholes

Table of Contents
Know Your Customer (KYC) protocols are the backbone of Anti-Money Laundering (AML) efforts, requiring financial institutions to verify their customers’ identities. However, criminals exploit KYC vulnerabilities, money launderers are relentlessly innovative, constantly probing for new vulnerabilities to bypass KYC checks and integrate their dirty cash into the legitimate financial system, often through these methods.
Account Opening Attacks
One common money laundering scheme involves criminals exploiting lax or automated customer onboarding processes to rapidly open scores of new accounts. Some fintech, crypto, and payment firms are marketing “super-fast” digital onboarding with minimal checks to attract more customers, but this creates vulnerabilities that enable criminal account-opening attacks.
Fraudsters spoof identity verification measures relatively quickly, including biometrics or video interviews. By utilising databases of forged or stolen identity documents to bypass document checks, criminals can gain control of hundreds of “money mule accounts” to funnel illicit funds that appear to be legitimate transactions.
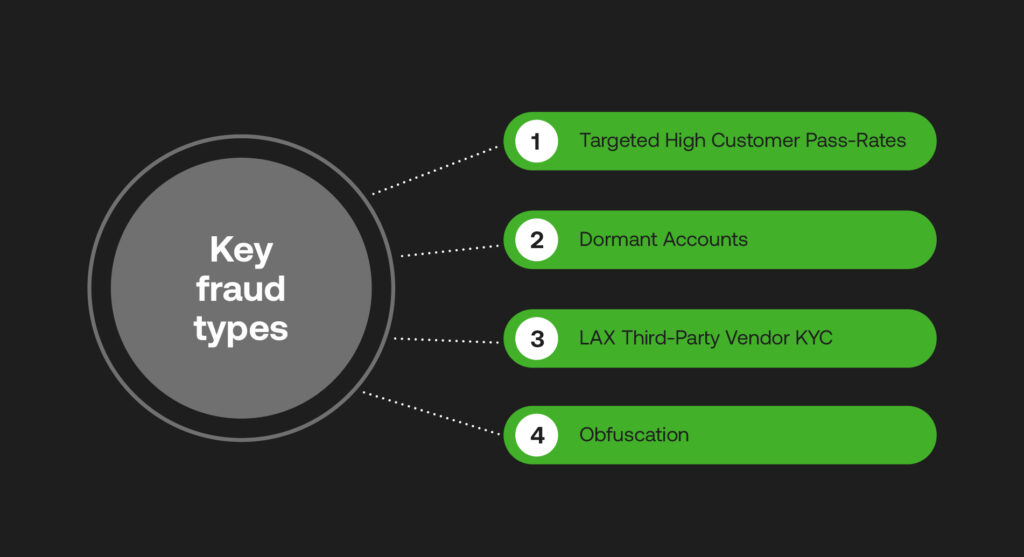
Targeted High Customer Pass-Rates
Shared KYC utilities and platforms promising high customer pass rates are particularly vulnerable without robust authentication controls. A sudden influx of new accounts opened could signal a criminal attack exploiting KYC gaps and loopholes.
These shared KYC services are an attractive target because they allow criminals to potentially open accounts across multiple financial institutions simultaneously by defeating the utility’s one-time checks. Without robust verification and continuous monitoring, bad actors can use tactics like synthetic identities, fake documents, and manipulated biometrics to impersonate legitimate customers during onboarding.
Suppose a KYC platform has lax or fully automated checks focused solely on quickly passing applicants. In that case, it creates openings for criminals to deploy automated scripts and bots that rapidly create and funnel through fraudulent accounts. These mule accounts can then deposit and move illicit funds across institutions that rely on the compromised utility.
Without supplementing it with additional due diligence and behavioural monitoring, overconfidence in shared KYC data exposes firms to regulatory penalties and reputational harm from falling victim to conspiracies exploiting these third-party onboarding weaknesses. Advanced analytics and identity intelligence are crucial for mitigating criminal account-opening attacks targeting shared KYC vulnerabilities.
Dormant Accounts
Dormant or inactive accounts that have already cleared KYC vetting present money laundering opportunities.
Launderers can purchase or gain control of dormant accounts and then reactivate them while avoiding additional screening. This method is particularly easy to exploit because dormant accounts had already gone through the entire KYC vetting process when first opened.
There are underground markets on the dark web where dormant bank accounts, payment services accounts, and other financial profiles can be bought. Fraudsters use techniques including taking over accounts from account holders or working with insiders to gain access. Some even compromise the accounts of deceased individuals.
Once they control a dormant account, criminals can update details like contact information and reactivate it with new funds flowing in from illicit sources. Since it’s an existing account, this reactivation often only triggers additional screening processes required by a brand-new account opening. This allows the launderers to bypass intense scrutiny over the true source of funds.
Lax practices around reviewing long-inactive accounts being revived make this a simple but highly effective method for integrating dirty money into the financial system under the radar. Banks and Fintechs must have processes to scrutinise dormant account reactivations as thoroughly as new applicants.
LAX Third-Party Vendor KYC
KYC requirements extend beyond a company’s direct customers to third parties like service providers, affiliates, and correspondent banking partners. Some criminal money laundering operations specialise in creating sham companies or recruiting money mules to exploit gaps from weaker third-party KYC programs, subsequently affecting the broader KYC process.
Obfuscation
Even when KYC checks are relatively robust, skilled money launderers utilise sophisticated obfuscation tactics to mask the origin of their dirty money. This includes techniques like smurfing (structuring cash deposits below reporting thresholds), trade-based laundering (under- or over-invoicing, misrepresenting goods), real estate investment purchases, casinos and gambling, gold, and complex corporate veils using shell companies and trusts.
Cyber Laundering
The digital realm has opened new frontiers that money laundering criminals are exploiting. “Cyber laundering” leverages tools like cryptocurrency tumblers and mixing services, online gaming and virtual asset trades, and dark web infrastructures to convert and transfer illicit proceeds anonymously online while avoiding KYC detection.
However, regulation around cyber laundering vectors like cryptocurrencies has struggled to keep pace with the rapid evolution of these technologies. Many jurisdictions still need more guidelines, allowing bad actors to capitalise on digital assets’ anonymity and decentralised nature.
This is where solutions like perpetual KYC (pKYC) can play a vital role. Unlike traditional one-time KYC checks, pKYC employs continuous monitoring and real-time screening of customer transactions, behaviours, and risk profiles. Advanced pKYC platforms can connect the dots between seemingly disparate virtual asset transfers, geo-track unexplained fund movements, and detect high-risk transactions before execution.
By maintaining persistent compliance vigilance, pKYC fills regulatory gaps and fortifies defences against cyber laundering through the latest technologies.
The South African Banxso Case: Exposing Risks of Digital Age Financial Crimes
Ongoing real-world cases prove the need for more intelligent KYC checks as the digital world accelerates.
One case involving Banxso highlights how easily criminals can exploit trusted platforms by leveraging emerging technologies to evade detection. Immediate Matrix was the criminal enterprise behind sophisticated financial scams that exploited Banxso’s platform and damaged its reputation, which created fraudulent deepfake advertisements featuring public figures to trick unsuspecting individuals.
These deceptive ads promoted fake investment opportunities and lured victims to click through to Banxso’s website, abusing Banxso’s credibility as a legitimate trading platform. However, the fraudulent deepfake content would disappear, allowing Immediate Matrix to cover its tracks.
By leveraging advanced technologies like deepfakes and cloaking techniques, Immediate Matrix perpetrated financial crimes under the guise of Banxso’s trusted brand. While Banxso claimed no direct involvement with Immediate Matrix, the company still faced significant reputational fallout from being unknowingly exploited as the vehicle for these nefarious schemes.
The Financial Sector Conduct Authority (FSCA) issued a warning against Immediate Matrix in December 2023, which abused Banxso’s credibility and used cloaking techniques to perpetrate sophisticated financial scams targeting Banxso’s users. While claiming no direct involvement with Immediate Matrix, Banxso still faces significant reputational damage from being the vehicle used in these highly challenging schemes for institutions to combat alone. Luckily, technology partners are helping them to fight back.
Accelerate Secure Customer Acquisition with RelyComply’s Advanced pKYC Platform
By harnessing machine learning, natural language processing, and data analytics capabilities, RelyComply’s single view AML platform empowers organisations to anticipate criminal tactics, protect customers, and mitigate reputational risks in today’s digital environment.
Our platform harnesses advanced technologies, including facial recognition, liveness detection, watchlist screening, and authoritative government data sources to establish customer identities comprehensively.
This allows you to:
- Prevent financial crimes by validating true identities
- Improve conversions with a fast, user-friendly onboarding experience
- Demonstrate compliance with the latest KYC/AML regulations
- Gain a centralised system for managing customer due diligence across jurisdictions
With RelyComply, you get the best of both worlds – highly automated ID proofing that satisfies stringent regulatory standards while expediting time-to-revenue with near-instant customer approval.
Disclaimer
This article is intended for educational purposes and reflects information correct at the time of publishing, which is subject to change and cannot guarantee accurate, timely or reliable information for use in future cases.